How are we tracked once we press play?
Surveillance and Video Games
Stephanie Vie and Jennifer deWinter
It seems a non sequitur to move from surveillance and privacy into talking about video games; after all, games are fun and engaging (Koster, 2004; deWinter, 2015a), they teach valuable literacies (Colby, Johnson, & Colby, 2013; Gee, 2007; Vie, 2008), and they offer creative avenues and expressions for students and faculty (Carbonaro et al., 2007; Wark, 2007). And with what Jesper Juul (2009) has called the casual revolution, people who never considered themselves game players have logged hours on touchscreen devices such as smart phones and tablets. How many of us, bored in a waiting room, have pulled out our phones and started crushing candy or finding the right word for our Words with Friends? Games are commonplace; they are part of our quotidian lives, and this is what situates them as an ideal portal for surveillance and data collection.
In our section of this webtext, we offer a quick statistical and economic summary of who plays these games, followed by a brief introduction to telemetric data collection. We then turn to three patterns of surveillance:
- peer surveillance and virality,
- corporate surveillance and game iteration, and
- government surveillance of suspected terrorist activities.
Game designers are taking note of these patterns of surveillance, so toward the end of this section, we discuss Jesse Schell's 2010 D.I.C.E. (Design, Innovate, Communicate, Entertain) talk in which he imagines a utopic world in which games make us better people. And while we recognize that much of this is scary doom-and-gloom stuff, we do want to end on a positive note. Once rule systems are in place and surveillance creates algorithms and databases, these systems can be gamed; so we end on this more positive note of resistance and agency within seemingly 1984-esque systems. As Laura Gonzales and Dànielle Nicole DeVoss articulate elsewhere in this webtext, our aim is not to scare off individuals from playing games—particularly given the many benefits that game play can bring to our lives such as increased motor and literacy skills, improved spatial attention, pronounced mental flexibility, and increased relaxation and joy.
Thus, our goal here is not to argue against games. Indeed, both of us are avid game players; we research, teach, design, and play video games. Instead, our goal is to broaden conversations about surveillance and privacy to consider games as technological agents within an ideological system that isolates and then rewards players for their good behavior and sharing patterns.
Who plays these games?
Facebook estimates more than 1 million monthly active users overall, and Facebook games are a major force in convincing people to log into their pages and spend time on the site. Millions of other gamers play on mobile devices like tablets, iPads, and smart phones. This graph from Statista shows U.S. summary numbers from 2011–2014 with projected data to 2019. Verified numbers for the US alone in 2014 is 146.6 million mobile phone gamers.
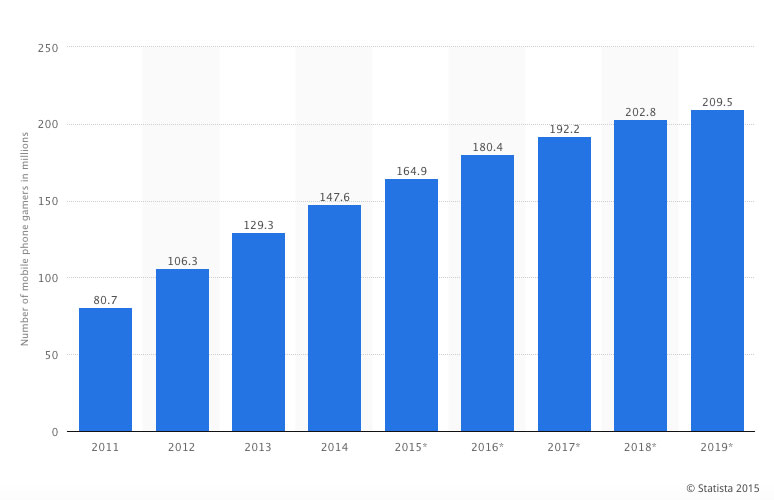
This is not just a U.S. phenomenon: Global game revenues show that mobile gaming will generate $30.3 billion worldwide, replacing console gaming as the top earner at $26.4 billion (Gaudiosi, 2015). And that's just mobile games. Console and PC gaming is increasingly played online, from MMORPGs like World of Warcraft to exercise games like Wii Fit. Within these frameworks, game designers and hosting companies rely upon user telemetry, a process that allows them to gather data on the behavior of players. These can come from, but are not limited to,
- • Game play
- • Purchasing behaviors
- • Physical movement
- • Interaction and communication with other users
- • Interactions with other applications.
Thus, while careful consideration has been given to freemium games and microtransactions (Grimes, 2015; Lescop & Lescop, 2014; Vie, 2014ab) and even to addictive gambling design components within these microtransactions (Gainsbury et al., 2014; deWinter 2015b), less attention has been paid to the changes in online culture because of surveillance and games. These changes do not affect just those who study games; they affect the ways that content hosting sites are run, the ways in which people participate in online communities, and even the types of data governments have access to.
Going Viral, or the Surveillance of Peers
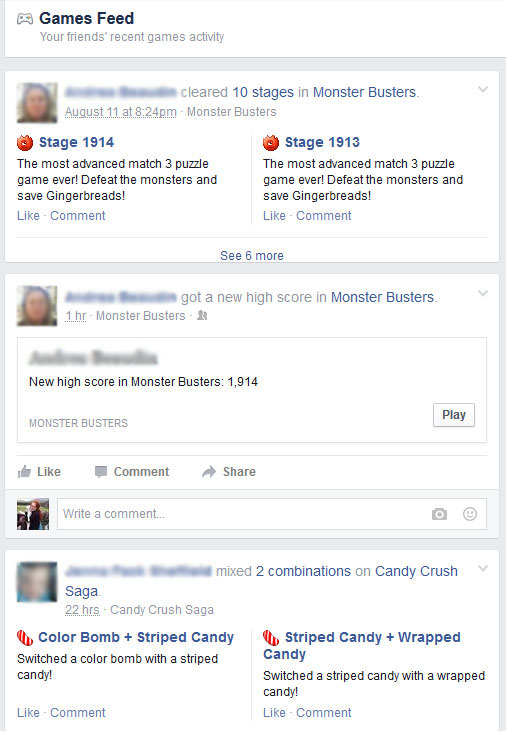
A number of games use social networks to increase player numbers by giving rewards and options to players only if they can bring a friend into the system. However, none have arguably been as successful as King's Candy Crush Saga. Candy Crush depends on viral marketing within social networks to increase its player base. For example, as the image below illustrates, when played by a player connected to Facebook, this game suggests automatic Facebook updates, allows you to always see how your friends are performing to drive competition, and encourages you to ask friends for help when stuck on a level.

This method of managed virality is a successful business strategy for many of these games, using friends to advertise the information through these simple status updates. Further, the scoreboard adheres to many of the basic values of competition, showing player scores juxtaposed to one another. In the image above, the player in the first position holds the number one spot on level 260 of Candy Crush with 418,840 points while Stephanie doesn't even appear on the first screen of the leaderboard given her score of 242,940 (placing her #24 among her Facebook friends).
Socially networked games leverage networked relationships to encourage new players to join the system and current players to compete with friends in the network. For example, Facebook's interface showcases a games feed that points out, play by play, what friends are accomplishing in the system. In the image below, viewers see the Facebook game activity of two of Stephanie's Facebook friends. Showing which levels they've beaten, what their current high scores in various games are, and even specific moves that they've made in these games, the Facebook games feed attempts to compel users to play and to compete with others in their network. Users may forget that Facebook will post automatically on their behalf unless they change their privacy settings; the site offers an anonymous game-play setting, which promises to let you "try out select games without sharing your Facebook info or letting games post to Facebook for you," but this option is turned off by default.
Within these socially networked games, competition is monetized through the offering of in-game boosters for a price ($0.99–$39.99) so that players can buy their way to higher scores against friends and family alike. While only about 30% of players of Candy Crush spend money, with over a billion downloads, this number is significant (Geron, 2013). In other words, surveillance is driving multiple economic sectors, which brings us to our next point.
From the Rules of the Game to the Rules of the Player, or the Surveillance of Corporations
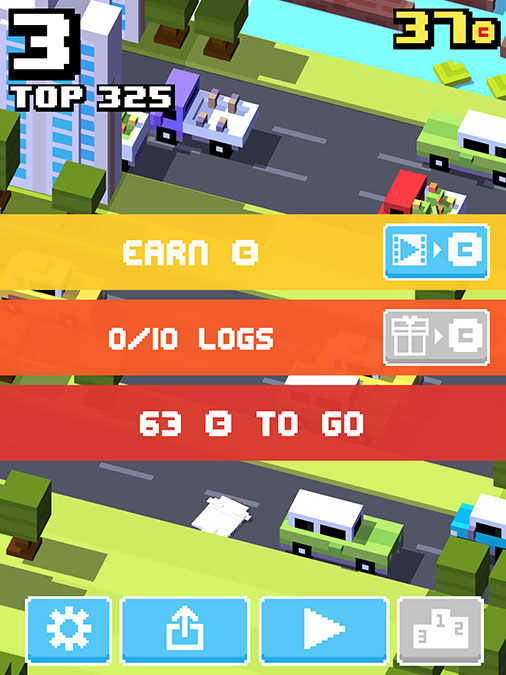
Using user telemetry, companies collect data on how players play in order to adapt the game for player experience. Further, these same companies track clicks, offer advertisements, and sell this data to other gaming and non-gaming companies. And in order to ensure that the user base keeps returning, companies use design strategies that compel players to take simple actions for points and free things (a point that Jesse Schell [2010] talks about as a positive force and which we take up later in this section). Often, these actions are tasks like watching advertisements or featured content in order to receive points, free moves or lives, in-game currency, or other digital valuables. The mobile game Crossy Road, an easy-to-play endless hopper game in the style of Frogger, offers players in-game currency (coins) in exchange for watching a number of videos advertising other games. At the time this screen shot was taken, the video being played promoted a new game, Paradise Bay, launched in March 2015 by King (the makers of Candy Crush Saga).
The exchange of our data for goods or services does not have to be problematic, but it often is when we are unaware that our data is being collected to begin with—or when we are unaware, as Colleen A. Reilly pointed out in her section of this webtext, that our data is being shared with third-party systems. As Estee N. Beck has questioned, the "rhetoric of sharing, of online networking, of connecting with others [has] led people to participate in algorithmic surveillance... people give up their data because of the perceived benefits of the product or service. Why is that?" (as cited in Lindgren, 2015). For many video games at least, the game space is deliberately crafted to highlight the fun, the excitement, the connectivity and to downplay elements of surveillance and data gathering.
The design of these games is so imbricated in the conditional levels of rhetoric that agency is either disguised (the game is offering me something, not a person designing the game) or disempowered (I didn't know that clicking yes would open me up to a ton of spam). Communication embeds purpose—monetization—into algorithmic systems of experience. The design and placement of the terms of service and privacy policies for these games is another area where agency is frequently disguised or disempowered. Frequently difficult to find, difficult to read, and difficult (if not impossible) to opt out of, the terms of service and privacy policies in mobile and socially networked games are another area where critical literacies of the kind espoused throughout this webtext (and throughout the conversations held in the Town Hall itself) become crucially important.
War Games, or the Surveillance of Governments
That games are closely aligned to war is not a new claim. They have been used to attract people to the military (such as the game America's Army) and to promote an ideology of war as heroic and good (Huntemann & Payne, 2009). However, seemingly disconnected games are now part of a larger war games strategy. For example, Mark Mazzetti and Justin Elliott (2013) found that the CIA, FBI, and Pentagon infiltrated World of Warcraft and collected information on Xbox Live. They wrote: "Fearing that terrorist or criminal networks could use the games to communicate secretly, move money or plot attacks, the documents show, intelligence operatives have entered terrain populated by digital avatars that include elves, gnomes and supermodels." And this isn't new. Doug Gross (2013) reported on a 2008 NSA memo that "called online gaming a 'target-rich communications network' where terrorists could communicate 'in plain sight'" (n.p.).
It's important to note here that, as games are increasingly part of U.S. daily life, they become a forum of civic space, of alternative fantasies, and of safe play. Many of these networked games provide spaces for people to get together and share common experiences. Increasingly, they offer a touch point in contemporary society as a cultural expression. As such, the implications of government spying are tremendous. Game theory often discusses the ways in which players assume a safe space, a place where the rules and consequences of a real world are suspended, whether that space is a magic circle a la Johan Huizinga (1955) or a protective psychological frame as proposed by Michael Apter (1989) and taken up by Steven Conway (2014). Play is a stress relief. It is less so if the government collects, stores, and interprets our data unbeknownst to us. And these rights extend to children playing on the Internet—rights that should be protected under the UN Right to Play. But legal cases have illustrated that game developers have failed to respect such rights in the past. A 2014 class action suit brought against game developer Zynga and Facebook claimed that users' identities and activities in Facebook games were disclosed to third parties without their consent; a 2012 suit settled against Playdom, Inc., fined the company $3 million after Playdom collected and disclosed personal information from hundreds of thousands of children under age 13 without parental consent (Vie, 2016, pp. 64–65).
Dystopian Future Presented as Utopian Future
What does it matter that games and play are surveilled? After all, almost everything that we do in contemporary society is watched and recorded, to how many steps we take in a day (thank you, iPhone and Fitbit) to what programs we like on Netflix. The problem is that surveillance can be used to create better games, better reward structures, better dopamine hits, and better consumer habits in us. Don't believe us? Watch this video of Jesse Schell's 2010 D.I.C.E. talk "Design Outside the Box":
Jesse Schell was an imagineer for Disney before becoming a game design professor at Carnegie Mellon University, and his work is excellent. This move to use games to fix the world, make people better, more happy, and healthier is not new. It comes from a contemporary fixation popularized by scholars such as Jane McGonigal (2011) and Ian Bogost (2011). What becomes eerily clear in these presentations, however, is the acceptance and use of game surveillance to change the human practices and cultures through technological means. What is being imagined is a system of constant distraction and external rewards—an almost perfectly realized culture industry. If only Adorno and Horkeimer knew about games and user telemetry.
Where is the Agency? Gaming the Masters of the Game
Gaming is not just something that hides an ideology of surveillance; gaming itself is an ideology. It shapes how we think of the world, affects our actions and opinions. So many people gamify activities that are not necessarily games, such as sales competitions, publication numbers, and even jogging times. What this means is that people can master the game. And if there is no game, people can use the points, numbers, rules, and affordances to imagine the game, and then master that game.
Take, for example, airline rewards points. Thanks to deregulation, airlines were able to come up with mechanism to reward fliers with points, frequent flier miles, and credit card offers. And for those who want to play, there are ways to always fly free in first class with all of the affordances available to them through these complex systems. Consider this story from Ben Wofford (2015) at Rolling Stone. Wofford focused on Ben Schlappig, a master travel hacker, writing:
Schlappig owes his small slice of fame to his blog "One Mile at a Time," a diary of a young man living the life of the world's most implausible airline ad. Posting as often as six times a day, he metes out meticulous counsel on the art of travel hacking—known in this world as the Hobby. It's not simply how-to tips that draw his fans, it's the vicarious thrill of Schlappig's nonstop-luxury life—one recent flight with a personal shower and butler service, or the time Schlappig was chauffeured across a tarmac in a Porsche. But his fans aren't just travel readers—they're gamers, and Schlappig is teaching them how to win.
And this idea of winning the game against the corporate bad guy permeates this text and the community that it represents. To succeed in these communities is to win, providing people a points system, win conditions, lose conditions, and narrative structure by repurposes the points and structures created through constant surveillance.
It is precisely the issue of agency that most intrigues us about the intersection of games and surveillance. Games offer multiple levels of inquiry into agency. From the beginning moments when a game is designed and developed, rhetorical awareness comes into play. Who will buy this game? Who will play this game? When and where will they play it, and why? And how long will it manage to capture their attention before they move on to another one? These questions seem easy enough to parse, and common enough for game designers who are interested in effective marketing.
It is the more difficult questions that interest us more, the questions that are trickier to answer because they involve greater numbers of stakeholders and incorporate legal statutes and ethical principles. For example, what kinds of data will be collected about players and when? How (or even will) players be notified about the personal data and game play data being collected from them? In what ways can players opt out of data collection yet still play the game? Will players have opportunities to help shape policy decisions about personal data collection, to provide feedback on the composition and placement of terms of service and privacy policies? Will they be effectively notified when their data is shared with third parties and will they be able to negotiate the sharing of that data in ways that are nuanced, not just binary options like yes or no?
What our conversations at the 2015 Computers & Writing Town Hall have illustrated is that our field is aware of and passionate about user agency with regard to privacy, surveillance, and data collection. From guiding students to think through the ways that data collection is rendered invisible, to considering the importance of a conceptual shift from assessing students as merely consumers to data producers and users, to thinking through position statements for writing program administrators concerned about the technologies of writing that surround us, the Town Hall showcased a lively conversation about these issues and more. Because they are fun, games are sometimes considered frivolous. To say that one has been playing games sounds less like work and serious business and more like, well... play. But games, as we have argued elsewhere (deWinter & Vie, 2015), are serious business. And as such, we argue that we should continue interrogating these important questions related to privacy, to personal data, to corporate surveillance, and to player agency in games. As rhetoricians and game players—and that is indeed what many of us are, whether we play Candy Crush, Final Fantasy, or simply Solitaire—we are well positioned to continue these conversations in ways that may make meaningful change in an activity that millions of us engage in every day.
References
Apter, Michael J. (1989). Reversal theory: Motivation, emotion and personality. London, England: Routledge.
Bogost, Ian. (2011). How to do things with videogames. Minneapolis, MN: University of Minnesota Press.
Carbonaro, Mike, Cutumisu, Maria, Duff, Harvey, Gillis, Stephanie, Onuczko, Curtis, Siegel, Jeff, & Waugh, Kevin. (2008). Interactive story authoring: A viable form of creative expression for the classroom. Computers & Education, 51(2), 687–707.
Colby, Richard, Johnson, Matthew S. S., & Colby, Rebekah Shultz. (Eds.). (2013). Rhetoric/composition/play through video games: Reshaping theory and practice of writing. London, England: Palgrave Macmillan.
Conway, Steven. (2014). Zombification?: Gamification, motivation, and the user. Journal of Gaming and Virtual Worlds, 6(2), 129–141.
deWinter, Jennifer. (2015a). Shigeru Miyamoto: Super Mario Bros., Donkey Kong, the Legend of Zelda. New York, NY: Bloomsbury.
deWinter, Jennifer. (2015b). Japan. In Mark J. P. Wolf (Ed.), Video games around the world (pp. 319–344). Cambridge, MA: MIT Press.
deWinter, Jennifer, & Vie, Stephanie. (2015). Sparklegate: Gamification, academic gravitas, and the infantilization of play. Kairos: A Journal of Rhetoric, Technology, and Pedagogy, 20(1). Retrieved January 1, 2016, from http://kairos.technorhetoric.net/20.1/topoi/dewinter-vie/index.html
Gaudiosi, John. (2015, January 15). Mobile game revenues set to overtake console games in 2015. Fortune. Retrieved from http://fortune.com/2015/01/15/mobile-console-game-revenues-2015/
Gee, James Paul. (2003). What video games have to teach us about learning and literacy. New York, NY: Palgrave Macmillan.
Geron, Tomio. (2013, March 26). How King.com zoomed up the social gaming charts. Forbes. Retrieved from http://www.forbes.com/sites/tomiogeron/2013/03/26/how-king-com-zoomed-up-the-social-gaming-charts/
Grimes, Sara M. (2013). From advergames to branded worlds: The commercialization of digital gaming. In Matthew P. McAllister & Emily West (Eds.), Routledge companion to advertising and promotional culture (pp. 387–399). New York, NY: Routledge.
Gross, Doug. (2013, December 10). Leak: Government spies snooped in 'Warcraft,' other games. CNN.com. Retrieved from http://www.cnn.com/2013/12/09/tech/web/nsa-spying-video-games/
Huizinga, Johan. (1955). Homo ludens: A study of the play-element in culture. Boston, MA: Beacon Press.
Huntemann, Nina B., & Payne, Matthew T. (Eds.). (2009). Joystick soldiers: The politics of play in military video games. New York, NY: Routledge.
Juul, Jesper. (2012). A casual revolution: Reinventing video games and their players. Cambridge, MA: MIT Press.
Koster, Raph. (2004). A theory of fun for game design. Phoenix, AZ: Paraglyph Press.
Lescop, Denis, & Lescop, Elena. (2014). Exploring mobile gaming revenues: The price tag of impatience, stress and release. Communications & Strategies, 94, 103–122.
Lindgren, Chris. (2015). Interview with digital rhetorician Estee Beck on algorithmic surveillance. University of Minnesota Codework Collaborative. Retrieved from http://umncodework.github.io/past_events/codework-interview-beck-digrhet-surveillance/
Gainsbury, Sally M., Hing, Nerilee, Delfabbro, Paul H., & King, Daniel L. (2014). A taxonomy of gambling and casino games via social media and online technologies. International Gambling Studies, 14(2), 196–213.
Mazzetti, Mark, & Elliott, Justin. (2013, December 9). Spies infiltrate a fantasy realm of online games. Retrieved from http://www.nytimes.com/2013/12/10/world/spies-dragnet-reaches-a-playing-field-of-elves-and-trolls.html
McGonigal, Jane. (2011). Reality is broken: Why games make us better and how they can change the world. New York, NY: Penguin.
Schell, Jesse. (2010). Design outside the box [Video]. Presentation at the D.I.C.E. Summit 2010. Retrieved January 1, 2016, from http://www.g4tv.com/videos/44277/dice-2010-design-outside-the-box-presentation/
Wark, McKenzie. (2009). Gamer theory. Cambridge, MA: Harvard University Press.
Wofford, Ben. (2015). Up in the air: Meet the man who flies around the world for free. Rolling Stone. Retrieved from http://www.rollingstone.com/culture/features/ben-schlappig-airlines-fly-free-20150720.
Vie, Stephanie. (2008). Are we truly worlds apart? Building bridges between Second Life and secondary education. Computers and Composition Online. Retrieved from http://www2.bgsu.edu/departments/english/cconline/gaming_issue_2008/Vie_Second_Life/
Vie, Stephanie. (2014a). "You are how you play": Privacy policies and data mining in social networking games. In Jennifer deWinter & Ryan Moeller (Eds.), Computer games and technical communication: Critical methods and applications at the intersection (pp. 171–187). Burlington, VT: Ashgate.
Vie, Stephanie. (2014b). Casual surveillance: Why we should pay attention to Candy Crush Saga and other casual games. First Person Scholar. Retrieved from http://www.firstpersonscholar.com/casual-surveillance/
Vie, Stephanie. (2016). Policies, terms of service, and social networking games. In Jennifer deWinter & Steven Conway (Eds.), Video game policy: Production, distribution, and consumption (pp. 54–67). New York, NY: Routledge.